FAQ
Open all
What is ransomware?
Ransomware is a malicious type of program that locks your computer, tablet, or smartphone — or encrypts your files and then demands ransom for their safe return. There are essentially two types of ransomware.
The first type is cryptors, which encrypt files so to make them inaccessible. Decrypting the files requires the key used to encrypt them — that’s what the ransom pays for.
The other type is called blockers; they simply block a computer or other device, rendering it inoperable. Blockers actually represent a better-case scenario than cryptors; victims stand a better chance of restoring blocked access than encrypted files.
How much is the usual ransom?
There really is no “usual.” However $300 that’s the average ransom extortionists ask their victims to pay to restore access to encrypted files or locked computers. But some ransomware programs ask for as little as $30. Some demand tens of thousands of dollars. Enterprises and other big organizations, which usually get infected through spear phishing, are more likely to receive higher ransom demands.
However, you should keep in mind that paying the ransom doesn’t ensure the safe and reliable return of files.
Can I decrypt the encrypted files without paying ransom?
Sometimes. The majority of ransomware programs use resilient crypto algorithms, which means that without an encryption key, decrypting them could take years.
Sometimes the criminals behind ransomware attacks make mistakes, enabling law enforcement to seize attack servers containing encryption keys. When that happens, the good guys are able to develop a decryptor.
How is ransom paid?
Usually, ransom is requested in cryptocurrency, namely bitcoins. This electronic currency cannot be forged. The history of transactions is available to anyone, but the owner of the wallet can’t easily be tracked. That’s why cybercriminals prefer bitcoins: They improve the odds of not getting caught.
Some types of ransomware use anonymous online wallets or even mobile payments. The most surprising method we have seen to date was $50 iTunes cards.
How does ransomware end up on my computer?
The most common vector is e-mail. Ransomware may pose as a useful or important attachment (an urgent invoice, an interesting article, a free app). Once you open the attachment, your PC is infected.
Ransomware can infiltrate your system while you’re just surfing the Internet, however. To gain control over your system, extortionists use OS, browser, or app vulnerabilities. That’s why it’s crucial you keep your software and operating system up to date (by the way, you can delegate this task to Kaspersky Premium, whose latest versions automate the process).
Some ransomware programs can self-propagate through local networks. If such a Trojan infects one machine or device in your home or enterprise network, other endpoints will also eventually get infected. But that is a rare case.
Of course, there are more predictable infection scenarios. You download a torrent, then you install a plugin…and away we go.
What kind of files are the most dangerous?
The most suspicious files are executables (like EXE or SCR), with Visual Basic scripts or JavaScript (.VBS and .JS extensions) not far behind. They are quite commonly packaged into ZIP or RAR archives to hide their malicious nature.
Another dangerous file category is MS Office files (DOC, DOCX, XLS, XLSX, PPT, and so forth). They may contain vulnerable macros; if you are prompted to enable macros in a Word document, think twice before you do it.
Be wary of shortcut files (.LNK extension) as well. Windows can depict them with any icon, which, paired with an innocent-looking file name, can lure you into trouble.
An important note: Windows opens files with known extensions without prompting the user, and by default it hides those extensions in Windows Explorer. So if you see a file named something like Important_info.txt, it could actually be Important_info.txt.exe, a malware installer. Set Windows to show extensions for greater security.
Can I avoid infection if I stay away from rogue websites or suspicious attachments?
Unfortunately, even cautious users can get infected with ransomware. For example, it’s possible to infect your PC while reading news on a big, reputable news website.
Of course, the website itself won’t distribute malware to visitors — unless it’s hacked, which is another story. Instead, advertising networks compromised by cybercriminals serve as distributors, and simply having an unpatched vulnerability lets malware load. Here again, having up-to-date software and a fully patched operating system are key.
I have a Mac, so I don’t need to worry about ransomware, right?
Macs can be and have been infected with ransomware. For example, KeRanger ransomware, which infiltrated the popular Transmission torrent client, hit Mac users.
Our experts believe that the number of ransomware programs targeting Apple systems will gradually increase. And with Apple devices being relatively expensive, extortionists may find Mac owners a great target for higher ransom demands.
Some types of ransomware even target Linux. No systems are safe from this threat.
I use my phone to go online. Do I have to worry about ransomware on Android?
You should. For example, cryptors and blockers for Android devices exist, with the latter being more prevalent. Having antivirus on your smartphone is not paranoid.

So, even iPhones are at risk?
To date, there are no dedicated ransomware programs for iPhone and iPad. That statement refers to iPhones that are not jailbroken, by the way. Malware can infiltrate devices that aren’t bound by the security restrictions of iOS and Apple’s locked-down App Store.
iPhone ransomware might be just around the corner, however, and not requiring a jailbroken system. We might see the emergence of IoT ransomware as well. Cybercriminals might demand high ransoms after taking over a smart TV or fridge.
How will I know if my computer gets infected with ransomware?
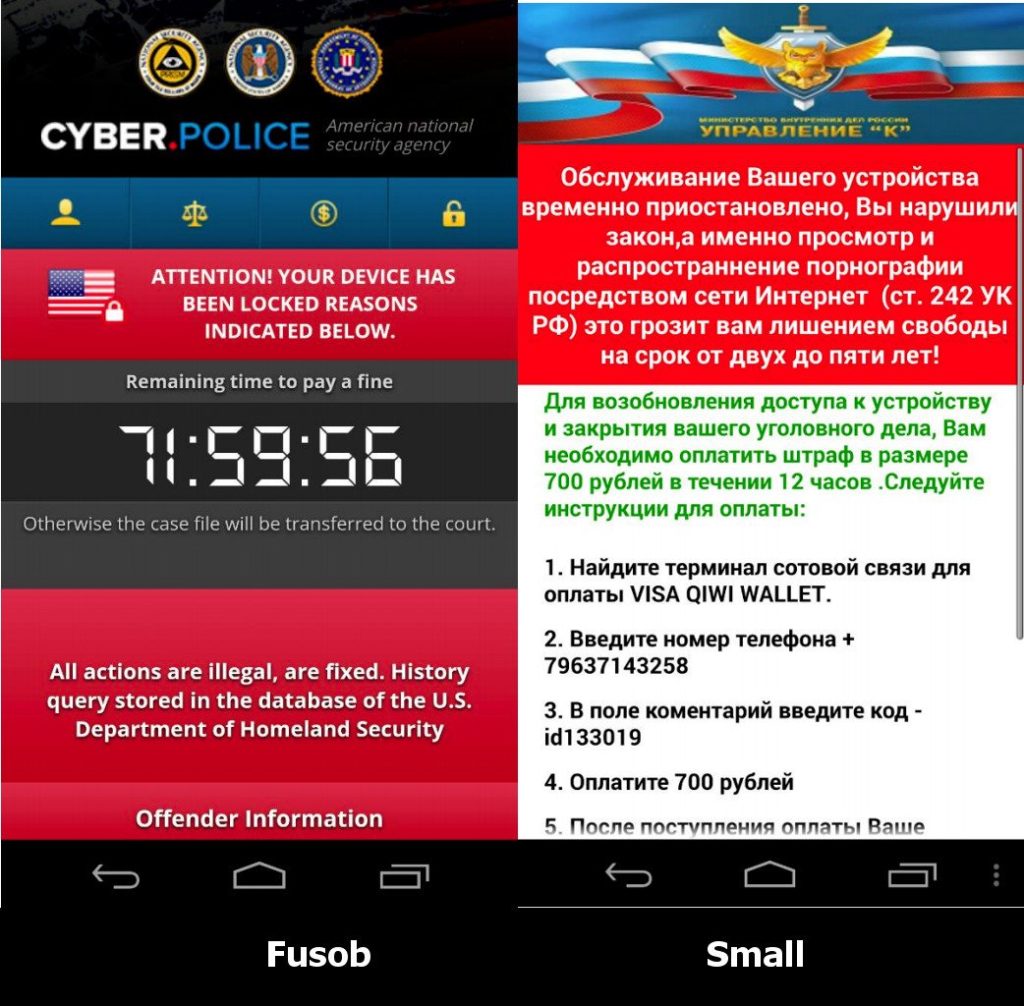
Ransomware isn’t subtle. It will announce itself, like this:
 Or this:
Or this:
 Or this:
Or this:
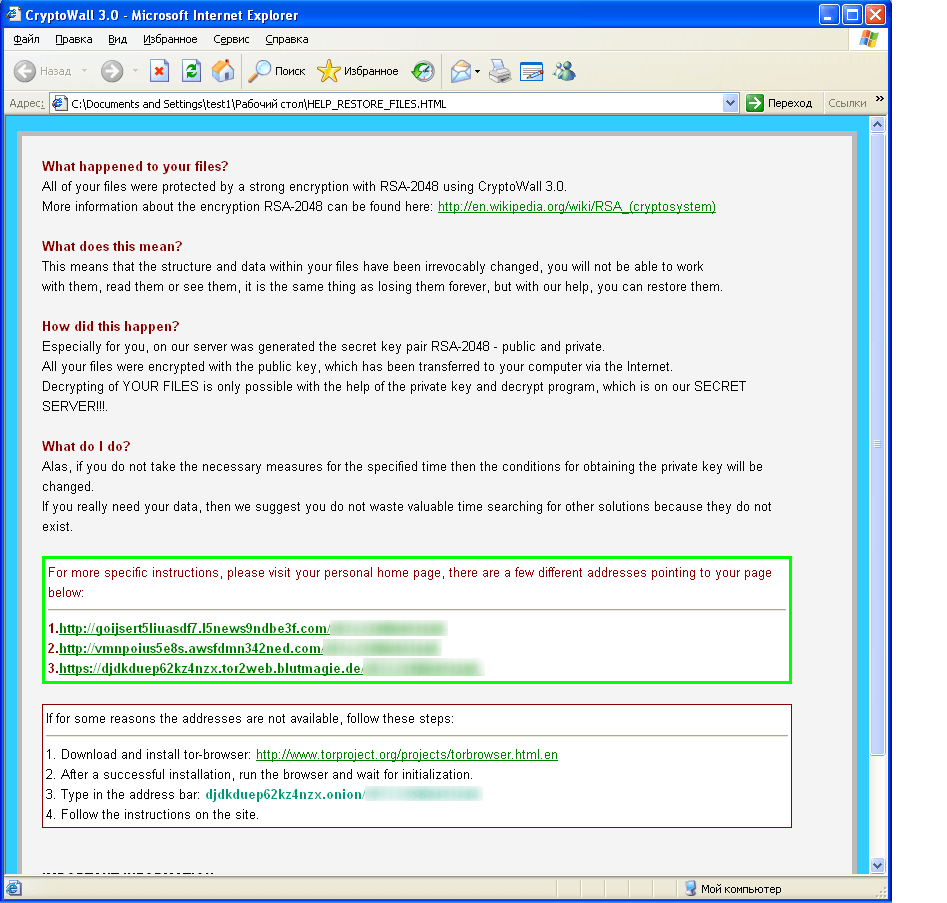
 Blockers look more like this:
Blockers look more like this:

 Or this:
Or this:
 Or this:
Or this:
 Blockers look more like this:
Blockers look more like this: 
Which ransomware types are the most prevalent?
New types of ransomware emerge every day, so it’s hard to say which are the most popular. We can enumerate several outstanding examples, such as Petya, which encrypts the entire hard drive. Also, there is СryptXXX, which is still powerful and which we took down twice. And, of course, TeslaCrypt was the most pervasive sample of ransomware for the first four months of 2016; its creators, unexpectedly, were the ones to publish a master key.
If I get infected, how to remove the ransomware?
If you find your computer blocked — it won’t load the operating system — use Kaspersky WindowsUnlocker, a free utility that can remove a blocker and get Windows to boot.
Cryptors are a harder nut to crack. First, you need to get rid of the malware by running an antivirus scan. If you don’t have a proper antivirus on your computer, you can download a free trial version here.
The next step is to get your files back.
If you have a backup copy of your files, you can simply restore your files from the backup. That is by far your best shot.
If you haven’t made backups, you can try to decrypt files by using special utilities called decryptors. All of the free decryptors created by Kaspersky can be found at Noransom.kaspersky.com.
Other antivirus companies also develop decryptors. One thing: Be very sure you’re downloading these programs from a reputable website; otherwise you run a high risk of getting infected by some other malware.
If you can’t find the right decryptor, you can pay the ransom or say good-bye to your files. That said, we don’t recommend paying the ransom.
Why not just pay the ransom?
For starters, there is no guarantee you will get your files back. You cannot trust extortionists. One example of untrustworthy thieves is the makers of Ranscam, ransomware that didn’t even bother with encrypting but simply deleted the files (although of course it promised decryption in exchange for money).
According to our research, 20% of ransomware victims who paid never got their files back.
I found the ransomware decryptor I need; why doesn’t it work?
Ransomware developers are quick to react when a new decryptor comes out, and they respond by modifying their malware to make it resilient to the available decryptor. It’s a game of whac-a-mole. Unfortunately, decryptors do not come with guarantees.
If I spot a malicious process, is there something I can do to stop the ransomware infection?
In theory, if you catch it in time, you can turn off the PC, remove the hard drive, insert it into another computer, and use that computer’s antivirus to disinfect. However, in real life it’s difficult or even impossible for a user to detect an infection; ransomware works quietly until the big reveal: the ransom note.
Is antivirus enough to avoid infection?
Yes, in the majority of cases. The antivirus solution you use matters, though. According to independent benchmarks by renowned labs (which are, in fact, the only benchmarks to trust), Kaspersky products offer better protection than the competition. However, no antivirus is 100% effective.
In many cases, automatic detection depends on how recent the malware is. If its signatures have not been added to antivirus databases, a Trojan can be detected with behavioral analysis. If it attempts to inflict damage, it’s blocked immediately.
Our product includes a module called System Watcher; if it detects an attempt of massive file encryption, it blocks the malicious process and rolls back all changes. Please never disable this component.
If I back up my files regularly, am I safe?
Backing up your files is very helpful, without a doubt, but it is not a 100% guarantee. Here’s one case: You set automatic backup on your spouse’s computer to run every three days. A cryptor infiltrates the system, encrypting all documents, photos, and so forth — but he does not get the gravity of the situation at once. So when you check in a week later, the backups are all encrypted, too. Backups are vitally important, but your defenses need to go further.
Are there any settings I can tweak to strengthen defenses?
a. First, do install an antivirus. But we have already told you that, haven’t we?
b. You can disable script execution in browsers, since they are a cybercrook’s favorite tool. Check out our blog to learn how to do that in Chrome and Firefox.
c. Make file extensions visible in Windows Explorer.
d. Make Notepad the default application for VBS and JS files. Windows usually marks dangerous VBS and JS scripts as text files, which can mislead less-savvy users into opening them.
b. You can disable script execution in browsers, since they are a cybercrook’s favorite tool. Check out our blog to learn how to do that in Chrome and Firefox.
c. Make file extensions visible in Windows Explorer.
d. Make Notepad the default application for VBS and JS files. Windows usually marks dangerous VBS and JS scripts as text files, which can mislead less-savvy users into opening them.
If you can't find a solution or it didn't work:
See FAQ
Ask Kaspersky Club for assistance in the "Help in the fight against ransomware" section
Ask for the tech support (only for Kaspersky’s paid products customers)